About Wifiphisher
Wifiphisher is a powerful and versatile rogue Access Point framework designed for red team engagements and comprehensive Wi-Fi security assessments. This tool enables penetration testers to effortlessly position themselves in a man-in-the-middle (MITM) scenario against wireless clients by executing targeted Wi-Fi association attacks. Beyond simple MITM attacks, Wifiphisher excels at deploying customized web phishing attacks against connected clients. This capability allows for the capture of sensitive credentials, such as those used for third-party logins or WPA/WPA2 Pre-Shared Keys. Furthermore, Wifiphisher can be leveraged to deliver malware payloads to unsuspecting victim devices.
Wifiphisher stands out due to its robust features and user-friendly design:
- Powerhouse Performance: Engineered for extended operations, Wifiphisher can reliably run for hours on resource-efficient devices like Raspberry Pi. It expertly employs a suite of contemporary Wi-Fi association attack methodologies, encompassing “Evil Twin,” “KARMA,” and “Known Beacons” techniques.
- Unmatched Flexibility: Adaptable to diverse scenarios, Wifiphisher boasts extensive argument support and a collection of community-developed phishing templates. This flexibility ensures it can be tailored to a wide array of deployment needs.
- Modular Architecture: Wifiphisher’s modular design empowers users to expand its functionality through custom Python modules. Whether creating simple extensions or intricate modules, the possibilities are vast. Users can also design bespoke phishing scenarios for highly targeted attacks.
- Ease of Use: Wifiphisher strikes a balance between advanced capabilities and user accessibility. While expert users can harness its rich feature set, beginners can initiate basic attacks with a simple command like “./bin/wifiphisher”. The intuitive Textual User Interface (TUI) guides users through each step of the attack configuration.
- Research-Driven Innovation: Wifiphisher is not just a tool; it’s a product of in-depth research. It incorporates groundbreaking attack techniques like “Known Beacons” and “Lure10,” pioneered by its developers, making it the first tool to integrate these advanced methods.
- Community Supported: Backed by a vibrant and supportive community of developers and users, Wifiphisher benefits from continuous improvement and collaborative development.
- Open Source and Free: Wifiphisher is freely available for download and use, distributed under the GPLv3 license. Its full source code is accessible, encouraging users to study, modify, and distribute it, promoting transparency and community contribution.
How Wifiphisher Operates
Wi-Fi phishing using Wifiphisher is a two-stage process:
1. Achieving Man-in-the-Middle (MITM) Position: The initial phase centers on establishing a MITM position by subtly associating with Wi-Fi clients. Wifiphisher employs various techniques to achieve this crucial step:
- Evil Twin Attack: Wifiphisher sets up a deceptive wireless network that mirrors a legitimate, trusted network, tricking users into connecting to the fake network.
- KARMA Attack: Leveraging the KARMA technique, Wifiphisher impersonates public networks that nearby Wi-Fi devices are actively searching for, creating an alluring honeypot.
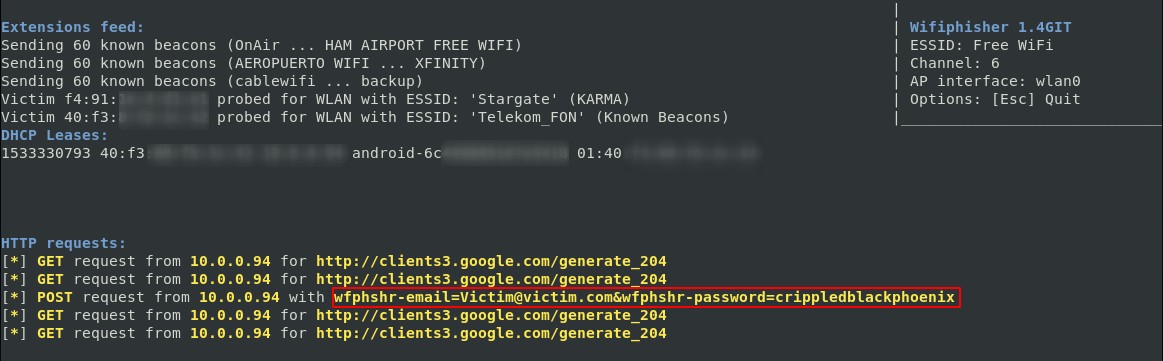
- Known Beacons Attack: This sophisticated method involves Wifiphisher broadcasting a list of common network names (ESSIDs) that devices in the vicinity have likely connected to before. This familiarity increases the chances of devices automatically connecting to the rogue access point.
Simultaneously with these techniques, Wifiphisher actively disrupts existing legitimate connections by sending “Deauthenticate” or “Disassociate” packets. This forces victims to disconnect from their intended networks, making them more susceptible to connecting to Wifiphisher’s rogue access point.
Performing MiTM attack
2. Web Phishing and Payload Delivery (Optional): Once a MITM position is secured, Wifiphisher opens up avenues for various attacks. While simple data sniffing and vulnerability scanning become possible, Wifiphisher truly shines in its advanced web phishing capabilities.
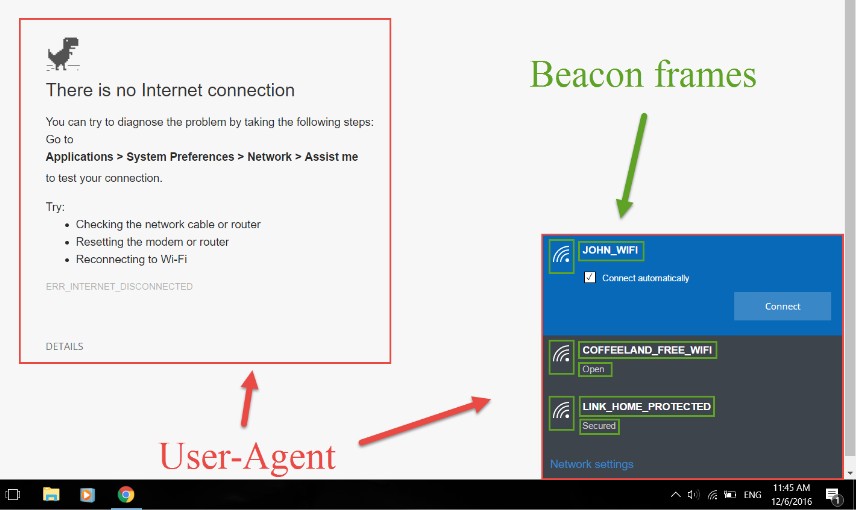
By intelligently gathering information from the target environment and the victim user’s device, Wifiphisher can craft highly convincing phishing pages. For instance, it can analyze broadcasted beacon frames and HTTP User-Agent headers to present a realistic, web-based imitation of a Windows network manager interface. This sophisticated approach is used to trick users into divulging sensitive information like Pre-Shared Keys or downloading malicious payloads.
Fake web-based network manager example, used in phishing scenarios.
System Requirements
To maximize Wifiphisher’s potential, ensure your system meets these requirements:
- Linux Operating System: While community members have reported success on various distributions, Kali Linux is the officially supported platform. New features undergo primary testing on Kali Linux to guarantee optimal performance and stability.
- Wireless Network Adapter with AP & Monitor Mode: Essential for Wifiphisher’s operations is a wireless network adapter that supports both Access Point (AP) and Monitor modes. Furthermore, it must be capable of packet injection. Driver compatibility with netlink is also a prerequisite.
Installation Guide
To install the most recent development version of Wifiphisher, execute the following commands in your terminal:
git clone https://github.com/wifiphisher/wifiphisher.git # Download the latest version
cd wifiphisher # Navigate to the Wifiphisher directory
sudo python setup.py install # Install dependencies and set up WifiphisherAlternatively, for users preferring stability, the latest stable release can be downloaded directly from the Releases page on the Wifiphisher GitHub repository.
Basic Usage Instructions
Execute Wifiphisher by simply typing wifiphisher or python bin/wifiphisher (when operating from within the tool’s directory) in your terminal.
Upon running without specific options, Wifiphisher intelligently identifies suitable wireless interfaces and interactively prompts you to select the ESSID of the target network from a list of available networks. You’ll also be asked to choose a phishing scenario. By default, Wifiphisher initiates both Evil Twin and KARMA attacks for comprehensive coverage.
Example Usage Scenarios:
- Manual Interface Selection and Firmware Upgrade Phishing:
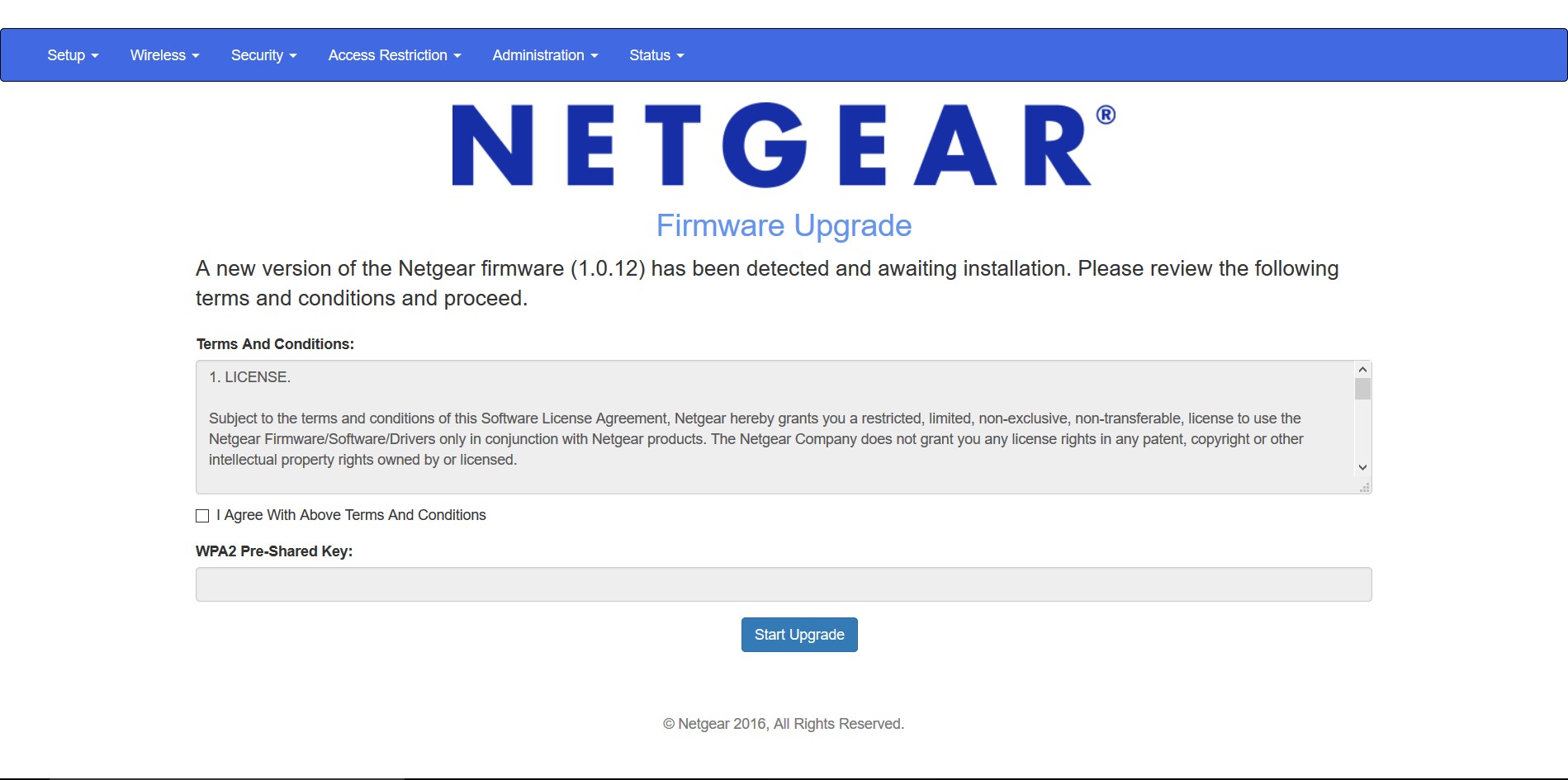
wifiphisher -aI wlan0 -jI wlan4 -p firmware-upgrade --handshake-capture handshake.pcapThis command utilizes wlan0 to create the rogue Access Point and wlan4 for initiating Denial of Service (DoS) attacks to disconnect targets from legitimate networks. It prompts manual selection of the target network and employs the “Firmware Upgrade” phishing scenario. The --handshake-capture option captures the WPA/WPA2 handshake for later verification of the captured Pre-Shared Key against the handshake.pcap file. The “Firmware Upgrade” scenario is particularly effective for obtaining network passwords.
- Automatic Interface Selection and Plugin Update Phishing:
wifiphisher --essid CONFERENCE_WIFI -p plugin_update -pK s3cr3tp4ssw0rdWifiphisher automatically selects appropriate interfaces in this scenario. It targets a Wi-Fi network with the ESSID “CONFERENCE_WIFI” and initiates the “Plugin Update” phishing scenario. The rogue Access Point is configured with WPA/WPA2 protection using the Pre-Shared Key “s3cr3tp4ssw0rd”. This is useful against networks with known passwords, like those in conferences. The “Plugin Update” scenario is ideal for tricking victims into downloading malicious files.
- Open Wi-Fi Network and OAuth Login Phishing with Known Beacons:
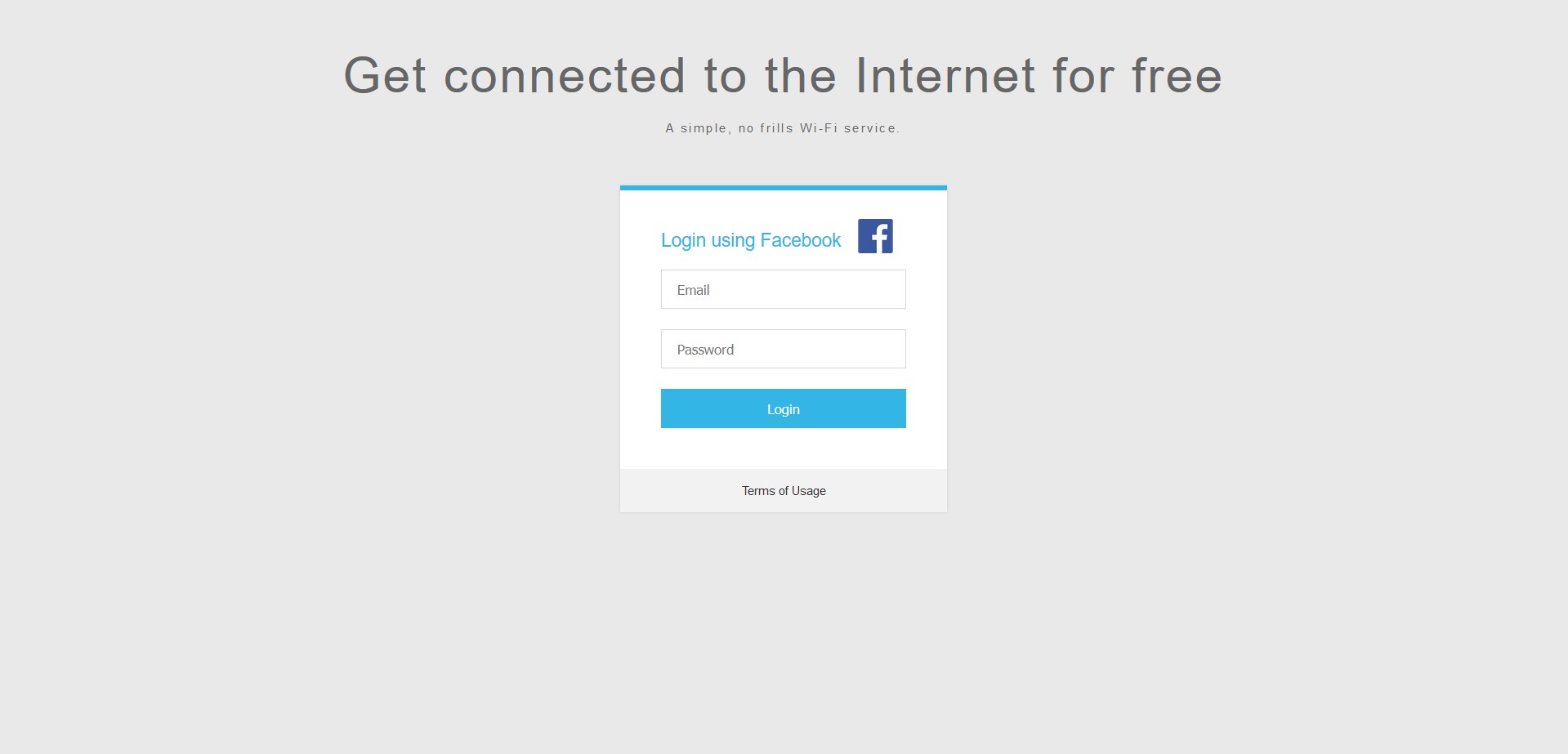
wifiphisher --essid "FREE WI-FI" -p oauth-login -kBThis command sets up an open Wi-Fi network named “FREE WI-FI” and deploys the “OAuth Login” phishing scenario. Additionally, it activates the “Known Beacons” technique for automatic Wi-Fi association, enhancing attack effectiveness. This is particularly effective in public areas. The “OAuth Login” scenario is designed to capture credentials from social media platforms like Facebook.
Wifiphisher Command Options:
| Short form | Long form | Description |
|---|---|---|
| -h | –help | Displays help message and exits. |
| -i INTERFACE | –interface INTERFACE | Manually specify an interface supporting both AP and monitor modes for rogue AP and extensions attacks. Example: -i wlan1 |
| -eI EXTENSIONSINTERFACE | –extensionsinterface EXTENSIONSINTERFACE | Manually select monitor mode interface for extensions. Example: -eI wlan1 |
| -aI APINTERFACE | –apinterface APINTERFACE | Manually choose AP mode interface. Example: -aI wlan0 |
| -pI INTERFACE | –protectinterface INTERFACE | Protect specified interfaces from NetworkManager control. |
| -kN | –keepnetworkmanager | Prevents Wifiphisher from killing NetworkManager. |
| -nE | –noextensions | Disables loading extensions. |
| -e ESSID | –essid ESSID | Sets ESSID for the rogue AP, skipping AP selection. Example: --essid 'Free WiFi' |
| -pPD PHISHING_PAGES_DIRECTORY | –phishing-pages-directory PHISHING_PAGES_DIRECTORY | Specifies custom phishing pages directory. |
| -p PHISHINGSCENARIO | –phishingscenario PHISHINGSCENARIO | Selects phishing scenario, skipping scenario selection. Example: -p firmware_upgrade |
| -pK PRESHAREDKEY | –presharedkey PRESHAREDKEY | Adds WPA/WPA2 protection to rogue AP with specified key. Example: -pK s3cr3tp4ssw0rd |
| -qS | –quitonsuccess | Exits after successful credential capture. |
| -lC | –lure10-capture | Captures BSSIDs during AP selection for Lure10 attack. |
| -lE LURE10_EXPLOIT | –lure10-exploit LURE10_EXPLOIT | Executes Lure10 attack to mislead Windows Location Service. |
| -iAM | –mac-ap-interface | Sets MAC address for AP interface. Example: -iAM 38:EC:11:00:00:00 |
| -iEM | –mac-extensions-interface | Sets MAC address for extensions interface. Example: -iEM E8:2A:EA:00:00:00 |
| -iNM | –no-mac-randomization | Disables MAC address randomization. |
| -hC | –handshake-capture | Captures WPA/WPA2 handshakes for verification (requires cowpatty). Example: -hC capture.pcap |
| -dE ESSID | –deauth-essid ESSID | Deauthenticates all BSSIDs with the specified ESSID. |
| -dC CHANNELS | –deauth-channels CHANNELS | Specifies channels for deauthentication. Example: --deauth-channels 1,3,7 |
| –logging | Enables logging to wifiphisher.log file. |
|
| -lP LOGPATH | –logpath LOGPATH | Sets custom log file path. |
| -cP CREDENTIAL_LOG_PATH | –credential-log-path CREDENTIAL_LOG_PATH | Sets custom credential log file path. |
| -cM | –channel-monitor | Monitors target AP for channel changes. |
| –payload-path | Enables payload path for scenarios serving payloads. | |
| -wP | –wps-pbc | Monitors WPS-PBC registrar button press. |
| -wAI | –wpspbc-assoc-interface | WLAN interface for WPS Access Point association. |
| -kB | –known-beacons | Activates Known Beacons Wi-Fi auto-association technique. |
| -fH | –force-hostapd | Forces usage of system-installed hostapd. |
| –dnsmasq-conf DNSMASQ_CONF | Sets custom dnsmasq.conf file path. |
|
| -dK | –disable-karma | Disables KARMA attack. |
| -pE | –phishing-essid | Sets custom ESSID for phishing page. |


Wifiphisher in Action: Screenshots
Interactive interface for targeting a specific access point during a Wifiphisher attack.
Screenshot of a successful Wifiphisher attack, demonstrating credential capture.
Example of a fake router configuration page served by Wifiphisher to capture network credentials.
Demonstration of a fake OAuth login page used in Wifiphisher for social media credential harvesting.
Visual example of a fake web-based network manager interface presented by Wifiphisher during an attack scenario.
Contribute and Get Involved
Your contributions can help enhance Wifiphisher! If you are a Python developer or possess web design skills, your expertise is highly valued. Explore the bug tracker for potential tasks and areas for improvement.
Even without coding skills, you can contribute by suggesting enhancements or reporting any bugs you encounter. Please consult the Bug Reporting Guidelines and the FAQ document before submitting reports. It’s important to understand the tool’s mechanics before reporting issues.
Credits and Acknowledgements
Wifiphisher’s foundation is based on an original concept by Dan McInerney from 2015.
For a comprehensive list of contributors, please visit here.
License Information
Wifiphisher is distributed under the GPLv3 license. For detailed license terms, refer to the LICENSE file within the repository.
Project Status and Updates
The current version of Wifiphisher is 1.4. Download the latest release from here or access the cutting-edge development version by cloning the repository.
Important Disclaimer
Using Wifiphisher to attack networks without explicit, prior consent is illegal and unethical. Users are solely responsible for adhering to all local, state, and federal laws. The authors of Wifiphisher disclaim any liability for misuse or damages caused by this tool.
Important Note: Exercise caution regarding websites claiming affiliation with the Wifiphisher Project, as they may distribute malware.
Stay updated on Wifiphisher news by following us on Twitter or liking our Facebook page.
